Adobe recently replied to the online discussion of Acrobat's vulnerability to brute-force attacks. Adobe claims that the specification for the 256-bit AES encryption in Acrobat 9 provides greater performance than the 128-bit implementation in previous versions. It is this improved performance that allows Acrobat 9 to open protected documents much more quickly.Adobe has admitted that brute-force attacks and dictionary-based password cracks benefit from the program's extra speed, because "fewer processor cycles are required" to test each password guess than with AES 128-encrypted documents. Adobe does not say how much faster attacks can be carried out, but Elcomsoft, a manufacturer of password-recovery tools, claims that passwords can now be cracked 100 times faster.To help mitigate dictionary attacks, Adobe advises customers to use long passwords or pass-phrases. Version 9 supports Unicode pass-phrases up to 127 characters in length. For even greater security, Adobe recommends using encryption based on the Public Key Infrastructure (PKI), although this requires the use of Adobe LiveCycle Rights Management.
Dec 4, 2008
Cracking Acrobat 9 Password
Dec 2, 2008
Patching via Command Line
- Create a list of server to be patched.
get-qadobject -sizelimit 0 -type computer | where {$_.osname -match "server"} | select name > c:\servers.txt
- Deploy the patch from a share folder.
psexec @serverlist.txt -c "\\File-Server\SecurityPatches$\MS08-067.exe /quiet /norestart /overwriteoem"
- Reboot the servers.
gc c:\servers.txt | ForEach-Object { gwmi win32_operatingsystem -ComputerName $_ | ForEach-Object { $_.reboot() }}
- Verify if any server failed the patching.
>>>> See Poor Mans Patching with PSExec and PowerShellfunction Get-HotFix($server,$hotFixID) {
PROCESS{
$results = gwmi win32_quickfixengineering -computer $_ -filter "HotFixID='$hotFixID'"
if ($results) {
$results | select CSName,HotFixID,@{n="Installed";e={"Yes"}}
} else {
$results = "" | select CSName,HotFixID,Installed
$results.CSName=$_
$results.HotFixID=$hotFixID
$results.Installed="No"
$results
}
}
}
gc (Read-Host "Please provide path to server list file") | Get-HotFix -hotFixID (Read-Host "Hotfix ID") | ft -auto
Nov 17, 2008
USB 3.0 to Transfer 25GB in 70 Seconds
USB 3.0 will be unveiled soon, and so far the new specs for the protocol look incredible, promising 25GB transfers in a mere 70 seconds. To put that in perspective, the same transfer would take 13.9 minutes with the current USB 2.0 protocol and 9.3 hours on USB 1.0.
Nov 14, 2008
HITB Material Archive is Online
- http://conference.hackinthebox.org/hitbsecconf2008kl/materials/
Nov 11, 2008
Security Event Correlation
Defining Security Event Correlation
This my final post discussing security event correlation (SEC) for now. (When I say SEC I do not mean the Simple Event Correlator [SEC] tool.)Previously I looked at some history regarding SEC, showing that the ways people thought about SEC really lacked rigor. Before describing my definition of SEC, I'd like to state what I think SEC is not.So, in my opinion -- you may disagree -- SEC is not:
- Collection (of data sources): Simply putting all of your log sources in a central location is not correlation.
- Normalization (of data sources): Converting your log sources into a common format, while perhaps necessary for correlation (according to some), is not correlation.
- Prioritization (of events): Deciding what events you most care about is not correlation.
- Suppression (via thresholding): Deciding not to see certain events is not correlation.
- Accumulation (via simple incrementing counters: Some people consider a report that one has 100 messages of the same type to be correlation. If that is really correlation I think your standards are too low. Counting is not correlation.
- Centralization (of policies): Applying a single policy to multiple messages, while useful, is not correlation itself.
- Summarization (via reports): Generating a report -- again helpful -- by itself is not correlation. It's counting and sorting.
- Administration (of software): Configuring systems is definitely not correlation.
- Delegation (of tasks): Telling someone to take action based on the above data is not correlation.
So what is correlation? In my last post I cited Greg Shipley, who said if the engine sees A and also sees B or C, then it will go do X. That seems closer to what I consider security event correlation. SEC has a content component (what happened) and a temporal component (when did it happen). Using those two elements you can accomplish what Greg says.
I'd like to offer the following definition, while being open to other ideas:
Security event correlation is the process of applying criteria to data inputs, generally of a conditional ("if-then") nature, in order to generate actionable data outputs.
So what about the nine elements are listed? They all seem important. Sure, but they are not correlation. They are functions of a Security Information and Event Management (SIEM) program, with correlation as one component. So, add correlation as item 10, and I think those 10 elements encompass SIEM well. This point is crucial:
SIEM is an operation, not a tool.
You can buy a SIEM tool but you can't buy a SIEM operation. You have to build a SIEM operation, and you may (or may not) use a SIEM to assist you.
Wait, didn't Raffy say SIM is dead? I'll try to respond to that soon. For now let me say that the guiding principle for my own operation is the following:
Not just more data; the right data -- fast, flexible, and functional.
Nov 7, 2008
SQLmap - Automatic SQL Injection Tool
Once it detects one or more SQL injections on the target host, the user can choose among a variety of options to perform an extensive back-end database management system fingerprint, retrieve DBMS session user and database, enumerate users, password hashes, privileges, databases, dump entire or user’s specific DBMS tables/columns, run his own SQL SELECT statement, read specific files on the file system and much more.
Nov 5, 2008
Grendel
The only system requirement is Java 5.
Tracking Gimmiv
- Only around 200 computers were infected since the time Gimmiv was actively deployed on September 29, 2008.
- Only 23 countries had infected users, and Southeast Asia appeared to have the greatest number of infections. Two networks in Malaysia had the most infections.
- While Malaysia was the hardest hit, it appears that the “in-the-wild” spread of Gimmiv may have started in Vietnam on September 29.
- The log shows that Gimmiv appeared first on August 20, 2008.
- A zip file left behind on one of the control servers contained Korean characters in the compressed folder name.
- One of IP addresses, located in Korea, was running Gimmiv in a VMware virtual machine (could be someone testing a piece of malicious mobile code to do).

Nov 4, 2008
Inside Uninformed Vol 10
This paper analyzes three vulnerabilities that were found in win32k.sys that allow kernel-mode code execution. The win32k.sys driver is a major component of the GUI subsystem in the Windows operating system. These vulnerabilities have been reported by the author and patched in MS08-025.The first vulnerability is a kernel pool overflow with an old communication mechanism called the Dynamic Data Exchange (DDE) protocol. The second vulnerability involves improper use of the ProbeForWrite function within string management functions. The third vulnerability concerns how win32k handles system menu functions. Their discovery and exploitation are covered.
This paper illustrates how IPv6-enabled systems with link-local and auto-configured addresses can be compromised using existing security tools. While most of the techniques described can apply to "real" IPv6 networks, the focus of this paper is to target IPv6-enabled systems on the local network.
Nov 3, 2008
lm2ntcrack
lm2ntcrack is Free and Open Source software. This sofware is entirely written in Perl, so its easily ported and installed.
* lm2ntcrack must be used with the password cracker John the Ripper.
WebSlayer
You can perform attacks like:
- Predictable resource locator, recursion supported
- Login forms bruteforce
- Session bruteforce
- Parameter bruteforce
- Parameter fuzzing and injection (XSS, SQL)
- Basic and Ntml authentication bruteforcing
Nov 1, 2008
Microsoft IT Compliance Management Guide
This is a new solution accelerator publichsed by Microsoft to help shifting IT governance, risk, and compliance (GRC) efforts from people to technology. It aims to help IT people to understand better on how to address GRC with an IT management framework implemented.
Click here for the IT Compliance Management Guide.
Published: October 29, 2008
About This Solution Accelerator
The IT Compliance Management Guide can help you shift your governance, risk, and compliance (GRC) efforts from people to technology. This Accelerator helps you better understand how an IT management framework can help you implement controls to address GRC requirements that apply to your organization. In addition, you can use its configuration guidance to help efficiently address your organization's GRC objectives.
The IT Compliance Management Guide is a Microsoft Operations Framework (MOF) 4.0 companion guide that is based on the Regulatory Compliance Planning Guide. It addresses GRC authority document requirements.
The IT Compliance Management Resources workbook provides an extensive inventory of GRC–related configuration and management guidance organized by Microsoft products.
"This guide contains the information that will enable IT professionals to have an informed discussion with their GRC subject matter experts, including legal and audit personnel. The overview of the audit process and descriptions of general GRC terminology and control concepts will allow IT professionals to be an active participant in these discussions. The associated workbook provides a comprehensive list of Microsoft resources that address GRC planning and product configuration topics relevant to IT professionals.
Oct 31, 2008
Web-Harvest
It leverages well established techniques and technologies for text/xml manipulation such as XSLT, XQuery and Regular Expressions. Web-Harvest mainly focuses on HTML/XML based web sites.
Gmail Modes
If you can't access Gmail, try some of these URLs:
Safe mode - http://mail.google.com/mail/?labs=0. It disables the experimental features from Gmail Labs, just in case some of them are buggy. You can remove some of the features from Gmail's settings page.
Secure mode - https://mail.google.com/. It encrypts the traffic between your computer and Gmail's servers. Use it from public computers, Wi-Fi networks or to bypass some proxies and web accelerators. There's a Gmail setting that redirects the standard version to the secure mode ("Always use https").
Older version - http://mail.google.com/mail/?ui=1. This version has been replaced in October 2007 by a rearchitectured Gmail, but the old version is a little bit faster.
Basic mode - http://mail.google.com/mail/?ui=html. It's the version that doesn't use JavaScript, so it loads faster and it works well with older browsers. Unfortunately, many Gmail features are missing (contacts autocomplete, chat, spell checker, rich formatting) and each click loads a new page. If you like this version, click on "Set basic HTML as default view" at the top of the page.
Mobile mode - http://mail.google.com/mail/?ui=mobile or http://m.gmail.com. This is a simplified Gmail interface for mobile phones that has even less feature than the basic mode. Use it if no other Gmail mode works for you.
iPhone mode - http://mail.google.com/mail/x/gdlakb-/gp/. A more user-friendly mobile version for iPhone and other mobile phones that use WebKit-based browsers.
iGoogle gadget - http://www.google.com/ig/gmailmax. This was mentioned here before. It is a canvas view for the updated Gmail gadget which can be found in the new iGoogle. Some people found that this interface bypasses most corporate filters that prevent them from accessing Gmail at work.
"No browser checking" mode - http://mail.google.com/mail?nocheckbrowser. If you use a cutting-edge new browser and Gmail serves you the basic HTML mode, try this URL to bypass browser detection.
Command Line mode - http://goosh.org/. This is for UNIX users.
Two Database Audit Tools
SQLAudit is made up of two .NET 2.0 Assemblies: SqlAudit.dll and SqlAuditGenerator.exe
T-SQL Script Generator for SQL Server 2000/2005 to Allow Auditing on Database Tables using Triggers and Additional tables for Auditing.
DBAudit Expert is a professional database auditing solution for Oracle, Sybase, DB2, MySQL and Microsoft SQL Server. DB Audit Expert enables database and system administrators, security administrators, auditors and operators to track and analyze any database activity including database security, access and usage, data creation, change or deletion. What makes DB Audit really unique is its built-in support for multiple auditing methods giving you the flexibility to choose the best fit for your database security requirements.
Oct 27, 2008
Microsoft Windows Azure
Windows® Azure is a cloud services operating system that serves as the development, service hosting and service management environment for the Azure Services Platform. Windows Azure provides developers with on-demand compute and storage to host, scale, and manage Web applications on the Internet through Microsoft® data centers.
We can use Windows® Azure to:
- Add Web service capabilities o existing packaged applications.
- Build, modify, and distribute applications to the Web with minimal on-premises resources.
- Perform services (large-volume storage, batch processing, intense or large-volume computations, etc.) off premises.
- Create, test, debug, and distribute Web services quickly and inexpensively.
- Reduce costs of building and extending on-premises resources.
- Reduce the effort and costs of IT management.
Oct 10, 2008
Comparing Smartphone OSes
Oct 6, 2008
Steganography Without Steganography Tool
Here's the step to follow:
- Prepare a innocent JPEG file and a list of confidential documents (pdf, doc, ppt, xls).
- Compress the list of confidential documents using any archiving tool, 7-zip, WinRAR, WinZIP, said confidential.7z (this works the same for RAR/ZIP/etc).
- Optional, you can remove the extension of the archive file if you want.
- Now issue the command to join the JPEG file and the archive file.
The new-innocent.jpg file will embed the confidential documents and is ready to be distributed. To retrieve the documents back, simply open the new-innocent.jpg file with any of the archiver tool and extract the files.
You will notice the size of the new-innocent.jpg is the total of the innocent.jpg and the confidential.7z.
If you open the new-innocent.jpg with any graphic editor, try to save it once, all your "attachments" will lost.
Oct 3, 2008
Cracking one billion passwords per second with NVIDIA video cards'
Cracking one billion passwords per second with NVIDIA video cards
Until recently, the abundance of highly parallel, super-scalar processors in 3D graphic accelerators could only be used for gaming. Today, ElcomSoft has found a way to reach into the future. The company has figured out how to put computational power provided by several NVIDIA boards working together to crack many kinds of passwords.
In February 2007, NVIDIA launched CUDA, a developer's kit that gives software developers access to the parallel processing power of the GPU. Modern NVIDIA GPUs act as powerful, highly parallel multiprocessors, with huge shared memory and cache.
Elcomsoft Distributed Password Recovery can recover a variety of system passwords such as NTLM and startup passwords, crack MD5 hashes, unlock password-protected documents created by Microsoft Office 97-2007, PDF files created by Adobe Acrobat, as well as PGP and UNIX and Oracle user passwords. With the newest GPU acceleration upgrade of Elcomsoft Distributed Password Recovery the passwords will be recovered up to 25 times faster than by using CPU-only mode.
Oct 2, 2008
Some Useless Google Chorme's Switches
- "-no-sandbox" allows Chrome to launch and work well, although with some diminished security in that each tab is not as restricted to its own sandbox.
- "-remote-shell-port=100". Not sure what you can do with it. But you can start telnet to localhost at TCP port 100 to get a Chrome prompt. No login is required.
Oct 1, 2008
SecApps

Sep 30, 2008
Cyber Security Awareness Month
- Preparation: October 1-4
- Identification: October 5-11
- Containment: October 12-18
- Eradication: October 19-25
- Recovery: October 26-31
- Lessons Learned: November 1-3
Sep 27, 2008
'Create a Bootable Ubuntu USB Flash Drive the Easy Way :: the How-To Geek'
This is a short instruction to create a bootable USB flash drive from Ubuntu ISO LiveCD. Why? Better speed.
>>>> From the page Create a Bootable Ubuntu USB Flash Drive the Easy Way :: the How-To Geek:
Create the Bootable Flash Drive
You'll first need to download the UNetbootin software and save it somewhere useful, since there's no installation required, just double-click to run.
I chose to use an already downloaded ISO image of the Ubuntu installation cd, and then chose my flash drive, and clicked the OK button. Yes, this step is as simple as that.

The process will extract the files from the ISO image (or download them), copy them to the flash drive and then install the bootloader. Depending on what you are installing, this really doesn't take very long.

Once the process is completed, you'll be prompted to reboot… which you don't necessarily have to do unless you want to test booting the flash drive on the same machine you are using.

Otherwise you can hit the Exit button.
Make Sure the Partition is Active
If you get a boot device error when you try and boot from the flash device, it could be that your partition is not marked as active. What we'll do is use the command line diskpart utility to fix this… if you are in Vista open an administrator mode command prompt by right-clicking and choosing Run as Administrator.
Now you'll need to run this command to figure out the number of your flash drive:
list disk
This will show you the list of drives, and you will use the disk number in the "select disk" command:
select disk 1
select partition 1
active
The "active" command will actually mark the current partition as active, which is why you need to select the disk and then the partition. At this point you should be done.
The Best Gmail Error Message
You can't get a funnier error message than this:
Dear valued user,
You have reached the error page for the error page...
You win!!
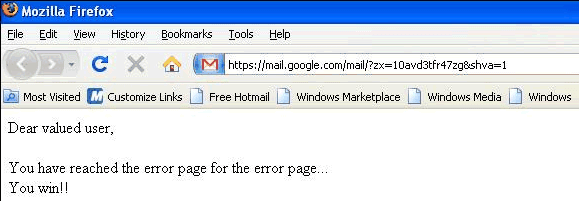
Sometimes even the error pages can't be displayed and you need to come up with a plan B. Gmail's meta-error page is simple, yet effective: Google can't always win.
This reminds me of a similar error message from Google Reader: "Oops! That wasn't supposed to happen".
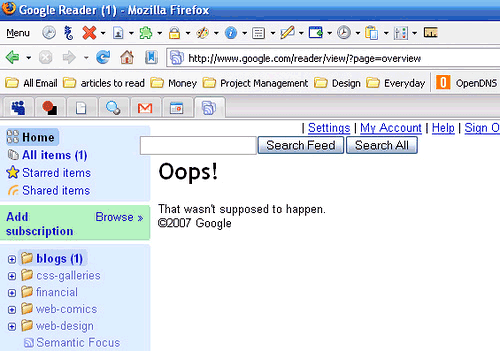
{ The first screenshot is licensed as Creative Commons Attribution-Noncommercial by Viofiddler. The second one is licensed as Creative Commons Attribution by Ashley Dryden. }
Cisco Bi-Annual Patch Day
As usual, SANS did a great job on summarizing the numerous vulnerabilities here with rating: 6 critical, 4 patch now, and 2 important. All the vulnerabilities can be exploited using readily available network utilities.
See also:
VMware Server 2 is Available
With VMware Server 2, the new features offer increased performance and stability. You benefit from:
- A broader range of guest operating system support.
- Direct access to virtual machine consoles.
- Intuitive Web-based management interface.
- More memory for greater scalability, from 3.6 GB to 8.0 GB of RAM per virtual machine.
Sep 26, 2008
XSS in Google Docs
Google Docs (HTML code) Multiple Cross Site Scripting Vulnerabilities
I. Background:
Google Docs is an online application which makes possibile to "Create and share your work online". You can use it to
create Documents, Presentations, Spreadsheets and Forms.
II. Description:
Multiple cross site scripting vulnerabilities were identified in Google Docs. A remote attacker could write a malformed
document and invite, through Google Docs sharing option, other users to see it in order to obtain their cookies. It's also possible
to public this malformed document and send its link around the web.
III. Details:
Google Docs makes possible to create a new document. When a user creates a new document he has the possibility to
change its html code through the Edit Html option. An attacker can make a malformed document using
decimal HTML entities (without semicolons) and hexadecimal entities (with semicolons) to bypass antixss filters.
Example:
<IMG SRC="javascript
:alert('test');"> (decimal HTML entity)
<IMG SRC="javascript
:alert('test');"> (hexadecimal HTML entity)
Please note: IMG tag isn't the only affected, it's just an example.
The attacker then will save his job and can share this document with someone else or send the document link to the victim to obtain his cookie.
IV. Vendor Response:
Google has been informed and has deployed a fix for these vulnerabilities.
V. Disclosure timeline:
- 23/08/08 - Vulnerabilities discovered
- 25/08/08 - Google informed
- 25/08/08 - Automatic reply from Google received
- 24/09/08 - Ask Google for updates
- 25/09/09 - Google fixed all vulnerabilities submitted
Regards
Alfredo Melloni
Chromium Snapshots
One of the solution is to download the daily snapshot from the following site:
Bonus is you get a portable Google Chrome browser.
Sep 23, 2008
Security Screen Saver
- Law #1: Nobody believes anything bad can happen to them, until it does
- Law #2: Security only works if the secure way also happens to be the easy way
- Law #3: If you don't keep up with security fixes, your network won't be yours for long
- Law #4: It doesn't do much good to install security fixes on a computer that was never secured to begin with
- Law #5: Eternal vigilance is the price of security
- Law #6: There really is someone out there trying to guess your passwords
- Law #7: The most secure network is a well-administered one
- Law #8: The difficulty of defending a network is directly proportional to its complexity
- Law #9: Security isn't about risk avoidance; it's about risk management
- Law #10: Technology is not a panacea
Sep 16, 2008
Use Multiple Google Accounts Simultaneously in Google Chrome
Google Chrome's incognito mode is less sophisticated than IE8's InPrivate browsing, but it has a feature that will be useful for those who have more than one Google account.
When you open a window in incognito mode (Ctrl+Shift+N), your cookies from the standard session are no longer available and you can easily log in to a new Google account.
Chrome's help center has more details about this feature. "Webpages that you open and files downloaded while you are incognito won't be logged in your browsing and download histories; all new cookies are deleted after you close the incognito window. You can browse normally and in incognito mode at the same time by using separate windows." Michael Jeffrey explains that "incognito mode is a window-level mode - all pages viewed within this window are not persisted to the user's history, and incognito pages use a temporary cookie store that is blank at the start of the incognito session".
When you close the incognito window, all the cookies are deleted so you need to log in again the next time you browse in incognito mode. This trick can be used for any other services that allow multiple accounts, but you can only use two accounts at the same time: one in a standard window and the other one in incognito mode.
Mystery Flaw in Google Docs
Till now, there is no way to re-produce the security flaw at the moment. It suspects the Google Docs flaw comes from a JavaScript error in how Google manages user sessions.
>>> http://blog.isc2.org/isc2_blog/2008/09/serious-securit.html
Sep 15, 2008
Zero-Day for QuickTime Round Up
The attack vectors for this bug is the access to malicious NetBIOS share is not filtered. So hypothetically all the applications which sends user-supplied file:// protocol URLs to FileProtocolHandler is vulnerable to the same attack.
QuickTime SMIL file, hosted at a malicious site, is the begin of the story. An attribute, called qt:next, within the SMIL file will instruct the QuickTime player to play the next mp3 file. This attribute can point to protocol handler such as http:// or file://
If the following URL is passed to the FileProtocolHandler using the attribute above:
And the content of the evil.lnk is point to the following JAR file:
Then it will bypass the following Windows protection and cause Java interpreter to execute the mailious JAR archive.
- XP SP1 and above will warn user that an application is launched from an untrusted share.
- This applies to all the executable extensions such as exe, .bat, .cmd, .vbs, .js, .application and other known executable file formats.
References:
Sep 11, 2008
The Ever Smallest ELF File
>>> http://www.muppetlabs.com/~breadbox/software/tiny/teensy.htmlThis 45-byte file is less than 1/8 the size of the smallest ELF executable we could create using the standard tools, and is less than 1/15 the size of the smallest file we could create using pure C code. We have stripped everything out of the file that we could, and put to dual purpose most of what we couldn't.
Of course, half of the values in this file violate some part of the ELF standard, and it's a wonder than Linux will even consent to sneeze on it, much less give it a process ID. This is not the sort of program to which one would normally be willing to confess authorship.
On the other hand, every single byte in this executable file can be accounted for and justified. How many executable files have you created lately that you can say that about?
Reset root's Password (with GRUB)
- Power up your machine and press ESC while GRUB menu starts.
- If there is a 'recovery mode' option, select it and press 'b' to boot into single user mode.
- Press 'e' (to edit) to the default menu option.
- Highlight the line with 'kernel' and press 'e' again.
- Append 'single' at the end of the line.
- Press 'b' to boot into single-user mode.
Note, some distribution might require you to re-mount the partition (with /etc inside) with read-write:
mount -o rw,remount /dev/hda1 /
- Boot the machine with a LiveCD.
- Search the partition that hold the /etc/passwd file: sudo fdisk -l
- Make a directory mount point: sudo mkdir /media/sda1
- Mount the partition with the mount point: sudo mount /dev/sda1 /media/sda1
- Change root to the mount point: sudo chroot /media/sda1
- Change the password: passwd root
Sep 7, 2008
10 Things to Help Fixing the Web
>>>> From GNUcitizen's Let's Fix the Web:
Here they are:
- Allow the user to sandbox and unsandbox applications and web resources with a single click
- Sandbox by default known applications such as GMail, Yahoo Mail, etc.
- In the sandbox, mark all cookies as
secureto prevent session leaks- In the sandbox, mark none-session cookies as
httpOnlyto prevent session hijacks due to XSS- Make sure that while on HTTPS, all embedded resources are delivered over HTTPS as well.
- Provide the option to turn off JavaScript, JAVA, Flash, SilverLight, etc on per-sandbox basis
- Block any external requests to sandboxed applications
- Implement the PHPIDS signature matching mechanism in JavaScript
- If the HTML structure is heavily broken, block the page to prevent some types of persistent XSS
- Record SSL signatures on trusted network and warn if signature changes while on untrusted network
Sep 5, 2008
Undocumented Switch in Google Chrome
Silent Crash PoC for Google Chrome
- http://myseq.blogspot.com/2008/09/google-chrome-first-0-day.html
- http://myseq.blogspot.com/2008/09/google-chrome-second-0-day.html
- View existing bugs at http://code.google.com/p/chromium/issues/list
More Tips on Google Chrome
- Google Chrome does support multiple profiles. Learn how to create separate profiles in Google Chrome at http://www.labnol.org/software/create-family-profiles-in-google-chrome/4394/
- If you are an impatient Linux user who want to give Google Chrome a try, see the instruction at http://www.myscienceisbetter.info/2008/09/install-google-chrome-on-linux-using-wine.html
- If you are a brave road-warrior, you may want to download the latest copy of Google Chrome at http://build.chromium.org/buildbot/snapshots/chromium-rel-xp/?O=D
- Right click on the BACK/FORWARD button to list the recently visited pages.
- Ctrl+Shift+T (Undo closing tab)
- Alt-D (Focus on omnibox bar)
- ? <query>
- Simple calculation with "5 miles in km"
- You can detach a tab by drag it outside the window.
- You can copy the downloaded file by drag it to desktop.
Avoid Re-activation of Windows XP (on same machine)
- Backup the file called "WPA.DBL", located in %systemroot%\system32 folder.
- Reinstall your XP, but decline the activation.
- Restore the WPA.DBL file to the same location.
Some Useful Google Talk Bots
Sep 4, 2008
Advanced Usages on Google Chrome
- about:
- about:version
- about:crash
- about:memory
- about:stats
- about:network
- about:internets (%systemroot%\system32\sspipes.scr)
- about:histograms
- about:dns
- about:cache
- about:plugins
- view-cache:[URL]
- view-source:[URL]
- Shift-Esc (Task Manager)
WiFi Vs. WiMax
| WiFi | WiMax | |
| Recommended Uses | Short-range, LAN-centric | Long-range, MAN-centric |
| Spectrum | Unlicensed spectrum 802.11b/g – 2.4 GHz 802.11n – 2.4 GHz, 5 GHz | Unlicensed or licensed spectrum between 2-66 GHz US: 2.4 GHz International: 2.3 GHz, 3.5 GHz |
| Quality of Service | Minimal - QoS is relative only between packets/flows | Guaranteed - QoS is assured using scheduling algorithms at MAC layer |
| Cell Footprint | < 300 meters maximum Most implementations about 30 meters | Up to 10 kilometers Most implementations about 3 km |
| Bandwidth | 802.11b: 11 Mbps max 802.11g: 54 Mbps max 802.11n: at least 100 MbpsAll bandwidth is at short range | Up to 70 Mbps theoretical max Up to 40 dedicated subscriber channels Expect 15 Mbps at 3 km range |
Google Chrome Second 0-Day
- POC at milw0rm.
- Another POC at raffon.net (also known as carpet-bombing flaw).
- Robert Hensing's Blog.
Sep 3, 2008
Google Chrome First 0-Day (in First Day)
Google Browser

- Simplified design with unifying web search, address bar, and history to one box.
- Show a visual sampling of your most visited sites every time you click on new tab.
- Use web applications without opening your browser.
- New incognito mode for private browsing.
- Individual sandbox design for every tab.
- Built-in task manager (Shift-Esc).
Aug 31, 2008
Something Can't Find by Google
>>>> Something You Can't Find Using Google:
Google Profiles, the public pages that include information about Google users, continue to add new questions. Some of the recent additions: "where I grew up", "where I live now", "places I've lived", "current company", "companies I've worked for", "current school", "schools I've attended", "my superpower".
There's even a metaphorical field "something I can't find using Google". What would you write if you were to answer that question in your Google profile?
See this for yourself now how many profiles are indexed by Google.
Aug 30, 2008
Full Access to Locked iPhone
- Enter the emergency call menu (of a locked iPhone).
- Double tap the HOME button (to open the Favorites menu).
The workaround for this flaw while waiting for the next firmware update:
- Simply enter the Settings menu on your iPhone
- Then enter General > Home Button
- Select “Home” or “iPod”.
Aug 26, 2008
BlackHat and Defcon Media Archives are Online
Security in MSIE8
Aug 25, 2008
RedHat Linux Compromised
This is an incredibly interesting vector of attack. Both releases of Red Hat Enterprise Linux v4, v5 and Fedora were modified with hackers essentially including their own key to the front door (ssh) into the operating system. If you have installed RHEL or Fedora from ftp or http sources recently you will certainly need to: "yum update".
Aug 22, 2008
IE and m4v file
m4v is an iTune Video file extension. See http://www.fileinfo.net/extension/m4v for more detail.
Aug 19, 2008
Microsoft Office 2007 Add-in: Microsoft Save as PDF or XPS
Aug 16, 2008
iPhone Screen Capture
With the new 2.0 firmware, you can take a screen capture using an easy key combo. Just hold down the home button and press the power button briefly. If you hold it for several seconds, the phone will soft reset, but if you just press and release, you'll see the screen flash and an image will be stored in your photos folder.
This ought to come in handy if you're doing any programming, web-based or native, on the iPhone.
See it in action at Youtube.
Aug 14, 2008
BSOD in Olympics Opening

Seems like the Windows XP Embedded (XPe) operating system has helped launch the 2008 Olympics in Beijing, but fails.

In case you never know what is BSOD, see some BSOD through ages. Or if you want to start customize your own BSOD, you may want to change the color and trigger it manually. Have fun!
Aug 7, 2008
Windows Vista(R) Performance and Tuning
Windows Vista and SP1 focus on delivering greater performance and overall system responsiveness. By striking a balance between speed and responsiveness, Windows Vista and SP1 deliver a level of performance that has the greatest positive impact on the system's usability.This guide looks at the following areas of performance improvement:
- Making configuration changes that help a computer feel more responsive when you use it.
- Using hardware to boost the actual physical speed of a computer.
- Making configuration changes that help a computer to start faster.
- Making the computer more reliable may help increase performance.
- Monitoring performance occasionally so that you can stop problems before they get too big.
File Extension in VMware
Some well-known file extensions used in VMware.
.VMDK -- These files are the actual hard disk of the virtual machine itself, and tend to be the largest file within the folder. You can consider the size of this file to be roughly equivalent to the size of either the disk itself (if you've chosen to use preallocated disks) or the size of the data currently stored on that disk (if you use growable disks).
.NVRAM -- Consider this file the BIOS of the virtual machine.
.VMX -- With typically one VMX file per folder, this file holds the configuration information for the virtual machine in a text format. Unlike almost all the other files you'll see, these files can be edited using any text editing program, a process that is actually required for some functionality that is not exposed in the GUI.
.VMXF -- This file, in XML format, includes additional information about the virtual machine if it has been added to a team. If a machine has been added to a team and then later removed, this file remains resident. This file can also be opened and read in a text editor.
.VMTM -- For virtual machines actively participating in a team, this file stores information about that team membership.
.VMEM -- These files, which contain a backup of the VMs paging file, are typically very small or non-existent when the virtual machine is powered off, but grow immediately to the size of configured RAM when the machine is powered on.
.VMSN and .VMSD -- When snapshots are created for a virtual machine, these files are created to host the state of the virtual machine. The VMSN file stores the running state of the machine, what you could consider the "delta" between the VMDK at the point of the snapshot and what has been processed up until the present time. The VMSD stores information and metadata about the snapshot itself.
.VMSS -- If you've suspected the state of your machine, this file contains the suspended state of that machine. These files typically only appear when virtual machines have been suspended.
Keep IPv6 Out of Windows Vista and Windows Server 2008
Not many people are familiar with IPv6 address scheme today. Sometimes, network troubleshooting in Windows Vista and Windows Server 2008 can be cumbersome. These OSs at times tend to give an IPv6 response to a network request instead of the IPv4 answer we're used to seeing. Two things you can do to keep IPv6 out of the picture for now.
Firstly, forces ping to use IPv4 for the request:
Secondly, disable IPv6 functionality entirely (via registry). Set the data for this value to 0xffffffff to disable all IPv6 components (except for the IPv6 loopback interface). This setting also configures the computer to prefer IPv4 over IPv6. Restart the computer for the setting to take effect.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\
DisabledComponents (DWORD): 0xffffffff
Aug 6, 2008
LiteNews Administrator Cookie Authentication Bypass Vulnerability
| Bugtraq ID: | 30555 |
| Class: | Design Error |
| Remote: | Yes |
| Published: | Aug 05 2008 12:00AM |
| Credit: | Scary-Boys |
| Vulnerable: | Wogan May LiteNews 1.2 |
| Description: | LiteNews is prone to an authentication-bypass vulnerability because it fails to adequately verify user-supplied input used for cookie-based authentication. Attackers can exploit this vulnerability to gain administrative access to the affected application. |
| Exploit: | Attackers can exploit this issue via a browser. The following example JavaScript code is available: javascript:document.cookie = "admin=1; path=/"; |
Aug 4, 2008
Backup or Restore Saved Network User Credentials in Windows Vista
Whenever you enter user credentials into Internet Explorer, map a drive to a remote server, or connect to a Windows domain, you are given the opportunity to save your password. What you may not realize is that you can backup or restore the list of those credentials using a mostly hidden control panel utility.
To open up this utility, type control userpasswords2 into the Start menu search box and hit enter.
On the resulting User Accounts screen, click on the Advanced tab and then click the Manage Passwords button.
You'll see the list of your stored network credentials here. For instance I've got saved credentials for all the remote desktop sessions that I use. (I don't have any web credentials in here because I use Firefox) You can click on the Add/Edit buttons if you feel like editing the items in the list.
To backup the list of user logon credentials, just click the Back up button, and a wizard will pop up.
Click the Browse button and choose a name for the file. Make sure it's something memorable. After you click the Next button you'll be taken to a somewhat strange screen.
That's right, you have to hit Ctrl+Alt+Delete to actually backup the credentials, and you'll be asked for a password to secure the file. Make sure it's something memorable or else you won't be able to restore the credentials later.
If you want to Restore the credentials from your backup, just click the Restore button, choose the backup file and then you'll be prompted to Ctrl+Alt+Delete again.
You'll be asked for the same password you created earlier, and the credentials will be restored.
The Only True Drop-in MS-Exchange Alternative
From the documentation, it seems impressive. It has 4 lines of product:
- PostPath Server
- PostPath Webmail
- PostPath Vmware Edition
- PostPath Archive Edition
Aug 3, 2008
Novell owns Unix's Intellectual Property
Here's how it works: Novell owns Unix's IP (intellectual property). SCO sold Unix's IP to Sun. Sun then included some Unix IP into Solaris. Finally, Sun open sourced Solaris as OpenSolaris. Sounds like trouble, doesn't it?Do you know since when Novell owns Unix's IP? What will happen if Novell start charging to Unix users one day?
Aug 1, 2008
Tricks to Make Linux Boot Faster
 ZDNet publishes an article about 10 tricks to make Linux boot faster.
ZDNet publishes an article about 10 tricks to make Linux boot faster.Linux rarely needs to be rebooted but, when it does, it often takes longer than you'd like. Below are the summary:
- Disable unnecessary services.
- Disable unnecessary kernel modules.
- Use a lightweight window manager, such as Enlightenment or Xfce, instead of Gnome or KDE.
- Use a text-based login instead of a graphical login.
- Use a lighter-weight distribution.
- Use an OpenBIOS - It allows Linux to actually initialize the hardware as it boots, instead of relying on the BIOS.
- Avoid DHCP.
- Get rid of hotplug - Note that udev has, for the most part, replaced hotplug. However, if you're running an older distribution, the above does apply.
- Try init-ng system (to replace SysVinit) - Decrease boot times in Unix-like operating systems.
- Use a hack with Debian - If you're using Debian, there is a simple hack you can use to switch your start up scripts to run in parallel. If you look at the /etc/init.d/rc script, you will see: 'Concurrency=none' around line 24. Change this line to 'Concurrency=shell' and you should see a reduction in boot times.
>>> http://resources.zdnet.co.uk/articles/features/0,1000002000,39454355,00.htm?r=16
How Not to Be Clueless CIO
As CIO, you hold one of the most important executive positions in your company. And, to lead successfully, you must earn the respect of both the business and your information technology organization. But earning the respect of application development professionals is no easy task: The CIO position has been a revolving door as of late and many application development professionals have become cynical.
>>> http://blackwhiteforest.blogspot.com/2008/08/nine-reasons-why-application-developers.html
Other readings:
Jul 30, 2008
Out of Cycle Security Update from Oracle
The emergency workaround, available here, addresses an unpatched vulnerability that's remotely exploitable without authentication (no username and password required to exploit over the network) and can result in compromising the confidentiality, integrity, and availability of the targeted system.
Oracle's Eric Maurice says the vulnerability carries a CVSS Base Score of 10.0, the maximum severity rating.
This IBM ISS alert provides some technical details:
Oracle WebLogic Server (formerly known as BEA WebLogic Server) is vulnerable to a buffer overflow, caused by improper bounds checking by the Apache Connector. By sending a specially-crafted HTTP POST request, a remote attacker could overflow a buffer and execute arbitrary code on the system or cause the server to crash.
Attributes in NTFS
Normally we will used to a few common attributes: Readonly, Archive, System, and Hidden. There are more than these actually. According to the documentation, we can have the following attributes for a file in NTFS: RASHCNETO.
- Readonly:
- For a file, applications can read the file, but cannot write to it or delete it.Applications can read the file but cannot write to it or delete it. For a directory, applications cannot delete it. * See here for more detail.
- Archive:
- The file or directory is an archive file. Applications use this attribute to mark files for backup or removal.
- System:
- The file or directory is part of the operating system, or is used exclusively by the operating system.
- Hidden:
- The file or directory is hidden. It is not included in an ordinary directory listing.
- Compress:
- The file or directory is compressed. For a file, this means that all of the data in the file is compressed. For a directory, this means that compression is the default for newly created files and subdirectories.
- Not content indexed:
- The file or directory is not to be indexed by the content indexing service.
- Encrypted:
- The file or directory is encrypted. For a file, this means that all data in the file is encrypted.For a directory, this means that encryption is the default for newly created files and subdirectories.
- Temporary:
- The file is being used for temporary storage. File systems avoid writing data back to mass storage if sufficient cache memory is available, because often the application deletes the temporary file shortly after the handle is closed. In that case, the system can entirely avoid writing the data. Otherwise, the data is written after the handle is closed.
- Offline:
You can check all these from here and here. See also Potential issues involved in updating Windows NT IFS drivers to Windows 2000.
- The data of the file is not immediately available. This attribute indicates that the file data has been physically moved to offline storage. This attribute is used by Remote Storage, the hierarchical storage management software. Applications should not arbitrarily change this attribute.
FILE_ATTRIBUTE_OFFLINEWhen this new attribute is set on a file, the network timeout on the file is extended from 45 seconds to 1000 seconds. (This new default value can in turn be changed via the registry setting System\CurrentControlSet\Services\LanmanWorkStation\Parameters\ OffLineFileTimeoutInterval.) This new attribute is supported in the Windows 2000 redirector (RDR). It may also be backported to a Windows NT 4.0 service pack at some point (it is not in SP4), and possibly a Windows 98 service pack. It is intended for use by devices with high latencies, such as tape or optical disk libraries.
Use and interpretation of FILE_ATTRIBUTE_OFFLINE is optional, except for filter drivers that perform volume scans. Such drivers should ignore offline files by default, although they may offer advanced users the option of including offline files in the scan.

