Here's the quick way to extract all the URL from a pcap file using tshark.
$ wget https://s3.amazonaws.com/tcpreplay-pcap-files/smallFlows.pcap
$ tshark -r smallFlows.pcap -T fields -e http.request.full_uri | grep -v "^$"
Here's the quick way to extract all the URL from a pcap file using tshark.
$ wget https://s3.amazonaws.com/tcpreplay-pcap-files/smallFlows.pcap
$ tshark -r smallFlows.pcap -T fields -e http.request.full_uri | grep -v "^$"
We all know Google Chrome browser is protecting users with Google Safe Browsing by alerting users for those malicious URLS.
Google Safe Browsing API is based on black list methodologies. With an API key, we can create an application to check URL against Google's lists of unsafe web resources. This is great for Cyber Threat Intelligence to scan the proxy log for suspicious social engineering sites or malware hosted URL.
A python library has been created for this at https://pypi.org/project/pysafebrowsing/
To install, just:
$ pip install pysafebrowsing
Just read the article about "Why You Need to Stop Using CVSS for Vulnerability Prioritization" from Tenable.
After using KennaSecurity, I learn that there is vulnerability management blindspot if you are using CVSS for vulnerability prioritization.
A simple scenario here:
The vulnerability scanning tool discovers 2 CVE at an external facing host (Debian OS): CVE-2020-8617 (cvss:5) and CVE-2020-1472 (cvss:9).
Conclusion: Asset priority is very important/useful while doing vulnerability prioritization. Make sure your vulnerability management tool does include any form of asset prioritization.
Just finished reading the full analysis report from Redscan. Although more vulnerabilities are on rise, there are still more positive signs based on the analysis. Here're some key takeaways:
Threat Intelligence data for Vulnerability Management:
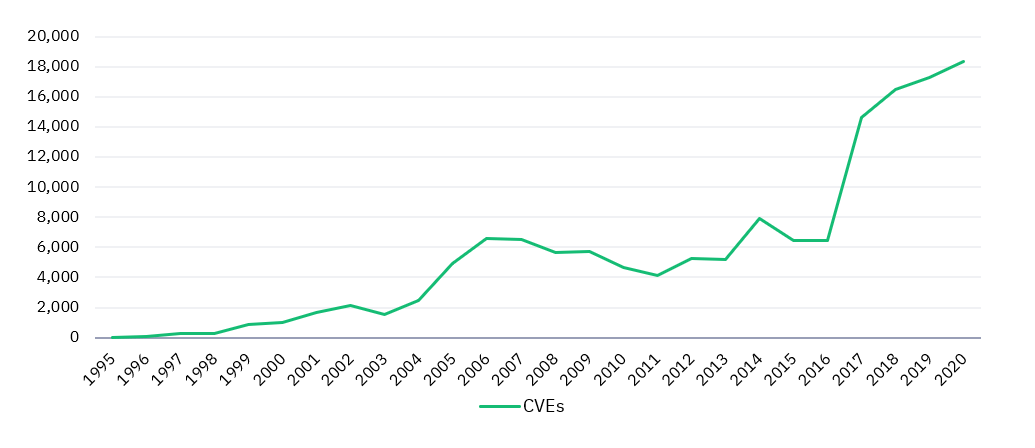 |
CVEs recorded by NIST NVD (1995-2020) |
Just discover a hidden search terms in Kenna today.
There is an undocumented Kenna search term that I think it is very useful: predicted_exploitable. It is boolean type for filtering vulnerabilities by those that have been predicted to be exploited based on Kenna proprietary algorithm.
We can customize a meter (or asset group) by "predicted_exploitable:true", in order to be more proactive/aggressive in prioritizing remediation.
This has been updated in Kenna Searching tips at Github.
Links:
Threat intelligence reporting is only useful if people read, comprehend, and take action on it. Because threat intelligence can be distributed and operationalized across an entire organization, from SOC analysts to the C-suite, it should be written for a broad audience.
In this SANS talk, Selena will take applications of journalism -- like the Inverted Pyramid style of news reporting, importance of a nutgraf, and killing passive voice -- to show attendees how she crafts clear, concise, and actionable threat intelligence reports.
The Frontline Workers are the first point of contact between organizations and their customers. As the face of your organization, their needs and wants should be prioritized first.
This webinar bring us some insightful views through the lens of Frontline Workers in APAC. Learn about the technology gaps that exist, the challenges they face with their current tools and what they truly need to do to put their best foot forward.
Just attended the webinar on Microsoft Security Hour, by Paula Januszkiewicz. This is the second webinar from her (this year), and this is about "The Power of Logs: Efficient Data Extraction Using Microsoft Solutions".
The webinar includes an excellent demo Azure Sentinel, and showing how she setup everything from scratch till creating the connectors and setting up the alert monitoring, within 20 minutes.
Is Agile software development a failed approach or is it an important advance?
Discussions of agile methodology and agile philosophy often get bogged down in discussions of practices:
In this episode, Dave Farley attempts to demystify agile thinking. What is the idea at the heart of agile thinking that made it definitively win the “waterfall vs agile” contest? Why is the idea of “post-agile” a misunderstanding of the step forward that the move to agile software engineering means for software development?
If Agile is used just because of predictability, then it is being used irrational, and have no difference than waterfall approach.
As part of February 2021 Patch Tuesday release, Microsoft released the final patch for Zerologon to enable a security setting by default to protect vulnerable systems.
CVE-2020-1472, also known as “Zerologon,” is a critical elevation of privilege vulnerability in Microsoft’s Netlogon Remote Protocol. It was initially patched in Microsoft’s August 2020 Patch Tuesday. The vulnerability received a CVSSv3 score of 10.0, the maximum possible score, and a Vulnerability Priority Rating (VPR) score of 10, underscoring its severity.
The first phase addressed the underlying vulnerability on two fronts. Firstly, patched DCs will block both Windows-based domain members and non-Windows DCs that are configured to explicitly disable signing/encryption. Secondly, the patch also changes the Netlogon protocol for clients unable to use the required signing/encryption.
With this final patch, it modifies the Netlogon Parameters registry key and enable Enforcement mode by setting the FullSecureChannelProtection data value to 1.
Additional links:
Today, I just converted an old python script to Windows executable file for myself.
It allows me to search assets based on hostname or IP address in Kenna at the command line. It also allow me to match a particular CVE and list all the vulnerabilities for the asset.
This is a strip down version where it only able to search assets within Kenna. (The full version can search within Kenna and R7 Nexpose). Below is the help screen:
| kenna-assets-win.exe -h |
Again, no source code nor executable package will be released at Github.