- Preparation: October 1-4
- Identification: October 5-11
- Containment: October 12-18
- Eradication: October 19-25
- Recovery: October 26-31
- Lessons Learned: November 1-3
Sep 30, 2008
Cyber Security Awareness Month
Sep 27, 2008
'Create a Bootable Ubuntu USB Flash Drive the Easy Way :: the How-To Geek'
This is a short instruction to create a bootable USB flash drive from Ubuntu ISO LiveCD. Why? Better speed.
>>>> From the page Create a Bootable Ubuntu USB Flash Drive the Easy Way :: the How-To Geek:
Create the Bootable Flash Drive
You'll first need to download the UNetbootin software and save it somewhere useful, since there's no installation required, just double-click to run.
I chose to use an already downloaded ISO image of the Ubuntu installation cd, and then chose my flash drive, and clicked the OK button. Yes, this step is as simple as that.

The process will extract the files from the ISO image (or download them), copy them to the flash drive and then install the bootloader. Depending on what you are installing, this really doesn't take very long.

Once the process is completed, you'll be prompted to reboot… which you don't necessarily have to do unless you want to test booting the flash drive on the same machine you are using.

Otherwise you can hit the Exit button.
Make Sure the Partition is Active
If you get a boot device error when you try and boot from the flash device, it could be that your partition is not marked as active. What we'll do is use the command line diskpart utility to fix this… if you are in Vista open an administrator mode command prompt by right-clicking and choosing Run as Administrator.
Now you'll need to run this command to figure out the number of your flash drive:
list disk
This will show you the list of drives, and you will use the disk number in the "select disk" command:
select disk 1
select partition 1
active
The "active" command will actually mark the current partition as active, which is why you need to select the disk and then the partition. At this point you should be done.
The Best Gmail Error Message
You can't get a funnier error message than this:
Dear valued user,
You have reached the error page for the error page...
You win!!
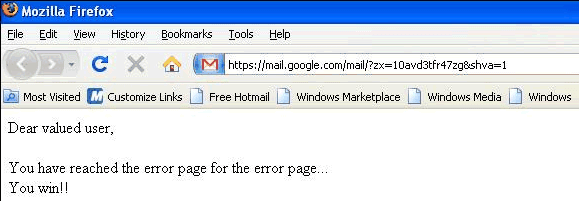
Sometimes even the error pages can't be displayed and you need to come up with a plan B. Gmail's meta-error page is simple, yet effective: Google can't always win.
This reminds me of a similar error message from Google Reader: "Oops! That wasn't supposed to happen".
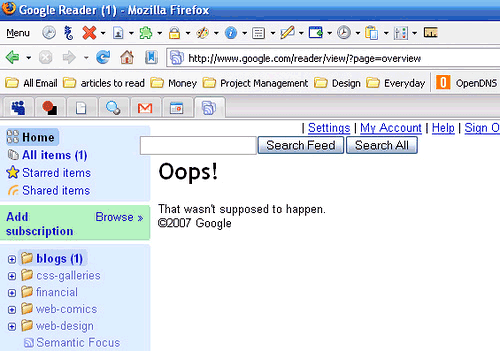
{ The first screenshot is licensed as Creative Commons Attribution-Noncommercial by Viofiddler. The second one is licensed as Creative Commons Attribution by Ashley Dryden. }
Cisco Bi-Annual Patch Day
As usual, SANS did a great job on summarizing the numerous vulnerabilities here with rating: 6 critical, 4 patch now, and 2 important. All the vulnerabilities can be exploited using readily available network utilities.
See also:
VMware Server 2 is Available
With VMware Server 2, the new features offer increased performance and stability. You benefit from:
- A broader range of guest operating system support.
- Direct access to virtual machine consoles.
- Intuitive Web-based management interface.
- More memory for greater scalability, from 3.6 GB to 8.0 GB of RAM per virtual machine.
Sep 26, 2008
XSS in Google Docs
Google Docs (HTML code) Multiple Cross Site Scripting Vulnerabilities
I. Background:
Google Docs is an online application which makes possibile to "Create and share your work online". You can use it to
create Documents, Presentations, Spreadsheets and Forms.
II. Description:
Multiple cross site scripting vulnerabilities were identified in Google Docs. A remote attacker could write a malformed
document and invite, through Google Docs sharing option, other users to see it in order to obtain their cookies. It's also possible
to public this malformed document and send its link around the web.
III. Details:
Google Docs makes possible to create a new document. When a user creates a new document he has the possibility to
change its html code through the Edit Html option. An attacker can make a malformed document using
decimal HTML entities (without semicolons) and hexadecimal entities (with semicolons) to bypass antixss filters.
Example:
<IMG SRC="javascript
:alert('test');"> (decimal HTML entity)
<IMG SRC="javascript
:alert('test');"> (hexadecimal HTML entity)
Please note: IMG tag isn't the only affected, it's just an example.
The attacker then will save his job and can share this document with someone else or send the document link to the victim to obtain his cookie.
IV. Vendor Response:
Google has been informed and has deployed a fix for these vulnerabilities.
V. Disclosure timeline:
- 23/08/08 - Vulnerabilities discovered
- 25/08/08 - Google informed
- 25/08/08 - Automatic reply from Google received
- 24/09/08 - Ask Google for updates
- 25/09/09 - Google fixed all vulnerabilities submitted
Regards
Alfredo Melloni
Chromium Snapshots
One of the solution is to download the daily snapshot from the following site:
Bonus is you get a portable Google Chrome browser.
Sep 23, 2008
Security Screen Saver
- Law #1: Nobody believes anything bad can happen to them, until it does
- Law #2: Security only works if the secure way also happens to be the easy way
- Law #3: If you don't keep up with security fixes, your network won't be yours for long
- Law #4: It doesn't do much good to install security fixes on a computer that was never secured to begin with
- Law #5: Eternal vigilance is the price of security
- Law #6: There really is someone out there trying to guess your passwords
- Law #7: The most secure network is a well-administered one
- Law #8: The difficulty of defending a network is directly proportional to its complexity
- Law #9: Security isn't about risk avoidance; it's about risk management
- Law #10: Technology is not a panacea
Sep 16, 2008
Use Multiple Google Accounts Simultaneously in Google Chrome
Google Chrome's incognito mode is less sophisticated than IE8's InPrivate browsing, but it has a feature that will be useful for those who have more than one Google account.
When you open a window in incognito mode (Ctrl+Shift+N), your cookies from the standard session are no longer available and you can easily log in to a new Google account.
Chrome's help center has more details about this feature. "Webpages that you open and files downloaded while you are incognito won't be logged in your browsing and download histories; all new cookies are deleted after you close the incognito window. You can browse normally and in incognito mode at the same time by using separate windows." Michael Jeffrey explains that "incognito mode is a window-level mode - all pages viewed within this window are not persisted to the user's history, and incognito pages use a temporary cookie store that is blank at the start of the incognito session".
When you close the incognito window, all the cookies are deleted so you need to log in again the next time you browse in incognito mode. This trick can be used for any other services that allow multiple accounts, but you can only use two accounts at the same time: one in a standard window and the other one in incognito mode.
Mystery Flaw in Google Docs
Till now, there is no way to re-produce the security flaw at the moment. It suspects the Google Docs flaw comes from a JavaScript error in how Google manages user sessions.
>>> http://blog.isc2.org/isc2_blog/2008/09/serious-securit.html
Sep 15, 2008
Zero-Day for QuickTime Round Up
The attack vectors for this bug is the access to malicious NetBIOS share is not filtered. So hypothetically all the applications which sends user-supplied file:// protocol URLs to FileProtocolHandler is vulnerable to the same attack.
QuickTime SMIL file, hosted at a malicious site, is the begin of the story. An attribute, called qt:next, within the SMIL file will instruct the QuickTime player to play the next mp3 file. This attribute can point to protocol handler such as http:// or file://
If the following URL is passed to the FileProtocolHandler using the attribute above:
And the content of the evil.lnk is point to the following JAR file:
Then it will bypass the following Windows protection and cause Java interpreter to execute the mailious JAR archive.
- XP SP1 and above will warn user that an application is launched from an untrusted share.
- This applies to all the executable extensions such as exe, .bat, .cmd, .vbs, .js, .application and other known executable file formats.
References:
Sep 11, 2008
The Ever Smallest ELF File
>>> http://www.muppetlabs.com/~breadbox/software/tiny/teensy.htmlThis 45-byte file is less than 1/8 the size of the smallest ELF executable we could create using the standard tools, and is less than 1/15 the size of the smallest file we could create using pure C code. We have stripped everything out of the file that we could, and put to dual purpose most of what we couldn't.
Of course, half of the values in this file violate some part of the ELF standard, and it's a wonder than Linux will even consent to sneeze on it, much less give it a process ID. This is not the sort of program to which one would normally be willing to confess authorship.
On the other hand, every single byte in this executable file can be accounted for and justified. How many executable files have you created lately that you can say that about?
Reset root's Password (with GRUB)
- Power up your machine and press ESC while GRUB menu starts.
- If there is a 'recovery mode' option, select it and press 'b' to boot into single user mode.
- Press 'e' (to edit) to the default menu option.
- Highlight the line with 'kernel' and press 'e' again.
- Append 'single' at the end of the line.
- Press 'b' to boot into single-user mode.
Note, some distribution might require you to re-mount the partition (with /etc inside) with read-write:
mount -o rw,remount /dev/hda1 /
- Boot the machine with a LiveCD.
- Search the partition that hold the /etc/passwd file: sudo fdisk -l
- Make a directory mount point: sudo mkdir /media/sda1
- Mount the partition with the mount point: sudo mount /dev/sda1 /media/sda1
- Change root to the mount point: sudo chroot /media/sda1
- Change the password: passwd root
Sep 7, 2008
10 Things to Help Fixing the Web
>>>> From GNUcitizen's Let's Fix the Web:
Here they are:
- Allow the user to sandbox and unsandbox applications and web resources with a single click
- Sandbox by default known applications such as GMail, Yahoo Mail, etc.
- In the sandbox, mark all cookies as
secureto prevent session leaks- In the sandbox, mark none-session cookies as
httpOnlyto prevent session hijacks due to XSS- Make sure that while on HTTPS, all embedded resources are delivered over HTTPS as well.
- Provide the option to turn off JavaScript, JAVA, Flash, SilverLight, etc on per-sandbox basis
- Block any external requests to sandboxed applications
- Implement the PHPIDS signature matching mechanism in JavaScript
- If the HTML structure is heavily broken, block the page to prevent some types of persistent XSS
- Record SSL signatures on trusted network and warn if signature changes while on untrusted network
Sep 5, 2008
Undocumented Switch in Google Chrome
Silent Crash PoC for Google Chrome
- http://myseq.blogspot.com/2008/09/google-chrome-first-0-day.html
- http://myseq.blogspot.com/2008/09/google-chrome-second-0-day.html
- View existing bugs at http://code.google.com/p/chromium/issues/list
More Tips on Google Chrome
- Google Chrome does support multiple profiles. Learn how to create separate profiles in Google Chrome at http://www.labnol.org/software/create-family-profiles-in-google-chrome/4394/
- If you are an impatient Linux user who want to give Google Chrome a try, see the instruction at http://www.myscienceisbetter.info/2008/09/install-google-chrome-on-linux-using-wine.html
- If you are a brave road-warrior, you may want to download the latest copy of Google Chrome at http://build.chromium.org/buildbot/snapshots/chromium-rel-xp/?O=D
- Right click on the BACK/FORWARD button to list the recently visited pages.
- Ctrl+Shift+T (Undo closing tab)
- Alt-D (Focus on omnibox bar)
- ? <query>
- Simple calculation with "5 miles in km"
- You can detach a tab by drag it outside the window.
- You can copy the downloaded file by drag it to desktop.
Avoid Re-activation of Windows XP (on same machine)
- Backup the file called "WPA.DBL", located in %systemroot%\system32 folder.
- Reinstall your XP, but decline the activation.
- Restore the WPA.DBL file to the same location.
Some Useful Google Talk Bots
Sep 4, 2008
Advanced Usages on Google Chrome
- about:
- about:version
- about:crash
- about:memory
- about:stats
- about:network
- about:internets (%systemroot%\system32\sspipes.scr)
- about:histograms
- about:dns
- about:cache
- about:plugins
- view-cache:[URL]
- view-source:[URL]
- Shift-Esc (Task Manager)
WiFi Vs. WiMax
| WiFi | WiMax | |
| Recommended Uses | Short-range, LAN-centric | Long-range, MAN-centric |
| Spectrum | Unlicensed spectrum 802.11b/g – 2.4 GHz 802.11n – 2.4 GHz, 5 GHz | Unlicensed or licensed spectrum between 2-66 GHz US: 2.4 GHz International: 2.3 GHz, 3.5 GHz |
| Quality of Service | Minimal - QoS is relative only between packets/flows | Guaranteed - QoS is assured using scheduling algorithms at MAC layer |
| Cell Footprint | < 300 meters maximum Most implementations about 30 meters | Up to 10 kilometers Most implementations about 3 km |
| Bandwidth | 802.11b: 11 Mbps max 802.11g: 54 Mbps max 802.11n: at least 100 MbpsAll bandwidth is at short range | Up to 70 Mbps theoretical max Up to 40 dedicated subscriber channels Expect 15 Mbps at 3 km range |
Google Chrome Second 0-Day
- POC at milw0rm.
- Another POC at raffon.net (also known as carpet-bombing flaw).
- Robert Hensing's Blog.
Sep 3, 2008
Google Chrome First 0-Day (in First Day)
Google Browser

- Simplified design with unifying web search, address bar, and history to one box.
- Show a visual sampling of your most visited sites every time you click on new tab.
- Use web applications without opening your browser.
- New incognito mode for private browsing.
- Individual sandbox design for every tab.
- Built-in task manager (Shift-Esc).
